In the realm of cybersecurity, Advanced Persistent Threats (APTs) represent a formidable challenge for organizations worldwide. Unlike traditional cyber attacks that aim for quick infiltration and data theft, APTs are sophisticated, targeted, and persistent, often orchestrated by well-funded and highly skilled threat actors. In this ongoing cyber warfare, firewall software emerges as a frontline defense mechanism, playing a crucial role in detecting, mitigating, and preventing APTs from compromising network security.
Understanding Advanced Persistent Threats (APTs)
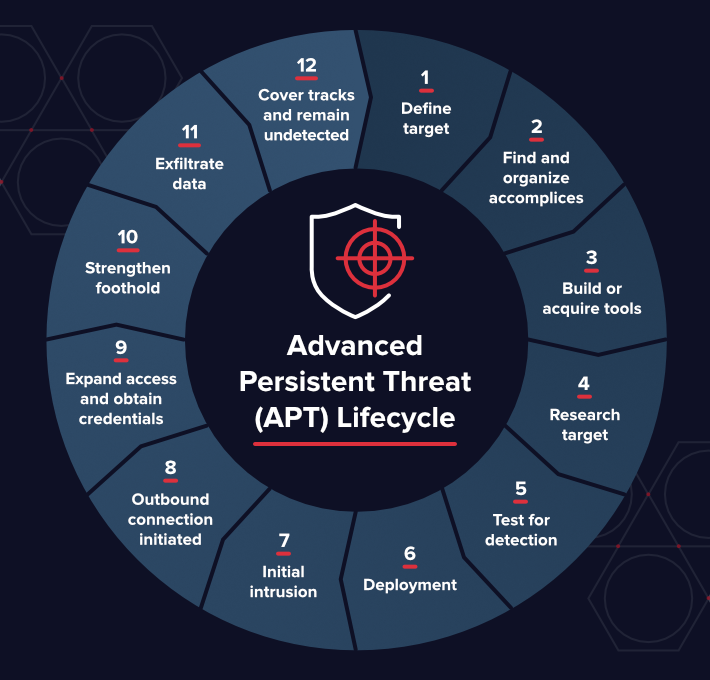
Advanced Persistent Threats (APTs) are stealthy and long-term cyber attacks designed to infiltrate networks, evade detection, and extract sensitive information over an extended period. Unlike opportunistic attacks, APTs are meticulously planned and executed by skilled adversaries, often state-sponsored actors, criminal organizations, or cyber espionage groups.
The modus operandi of APTs typically involves multiple stages, including reconnaissance, initial compromise, lateral movement, privilege escalation, data exfiltration, and persistence. These attacks are characterized by their persistence, adaptability, and ability to remain undetected for extended periods, making them particularly challenging to combat.
Role of Firewall Software in APT Defense
Firewall software serves as a critical component in the defense against APTs, providing essential capabilities for detecting, blocking, and mitigating these sophisticated attacks. While traditional firewalls primarily focus on filtering network traffic based on predefined rules, modern firewall solutions, such as Next-Generation Firewalls (NGFWs), incorporate advanced features specifically designed to combat APTs:
- Intrusion Prevention Systems (IPS): IPS functionality within firewall software enables real-time detection and prevention of known and unknown threats by inspecting network packets for suspicious patterns or behaviors. By employing signature-based detection, anomaly detection, and heuristics, IPS helps identify and block APT-related activities before they can penetrate the network perimeter.
- Application Control: APTs often exploit legitimate applications and protocols to blend into normal network traffic and evade detection. Firewall software with application control capabilities allows administrators to granularly control and monitor the use of applications within the network, thereby reducing the attack surface and preventing unauthorized access.
- Deep Packet Inspection (DPI): DPI enables firewall software to inspect the contents of network packets at the application layer, allowing for more thorough analysis of traffic and identification of APT-related threats. By examining packet payloads and comparing them against known attack signatures or behavioral patterns, DPI helps detect and block APT activities that may otherwise go unnoticed.
- Behavioral Analysis: Advanced firewall solutions incorporate behavioral analysis techniques to identify deviations from normal network behavior indicative of APT activity. By establishing baselines of normal network behavior and continuously monitoring for anomalies, firewall software can raise alerts or take preventive actions in response to suspicious activities associated with APTs.
Enhancing APT Defense with Network Segmentation
In addition to leveraging firewall software, organizations can further strengthen their defenses against APTs by implementing network segmentation strategies. Network segmentation involves dividing a large network into smaller, isolated segments or zones, each with its own set of security policies and access controls. By compartmentalizing the network and restricting lateral movement between segments, organizations can limit the impact of APTs and prevent them from spreading laterally across the network.
Firewall software plays a crucial role in enforcing segmentation policies, controlling traffic flows between network segments, and monitoring communications to detect any unauthorized attempts to breach segmentation boundaries. By combining firewall-based segmentation with other security measures such as encryption, multi-factor authentication, and endpoint detection and response (EDR) solutions, organizations can create layered defenses that effectively mitigate the risks posed by APTs.
Conclusion
In the face of increasingly sophisticated and persistent cyber threats such as Advanced Persistent Threats (APTs), organizations must adopt a multi-faceted approach to cybersecurity that leverages advanced technologies and best practices. Firewall software, with its advanced features and capabilities, serves as a cornerstone of APT defense, enabling organizations to detect, block, and mitigate APT-related activities effectively. By deploying firewall solutions equipped with intrusion prevention, application control, deep packet inspection, and behavioral analysis capabilities, organizations can bolster their security posture and safeguard their networks against the pervasive threat of APTs.